Introduction to Computer Networking
Network Applications
Read and write data over network
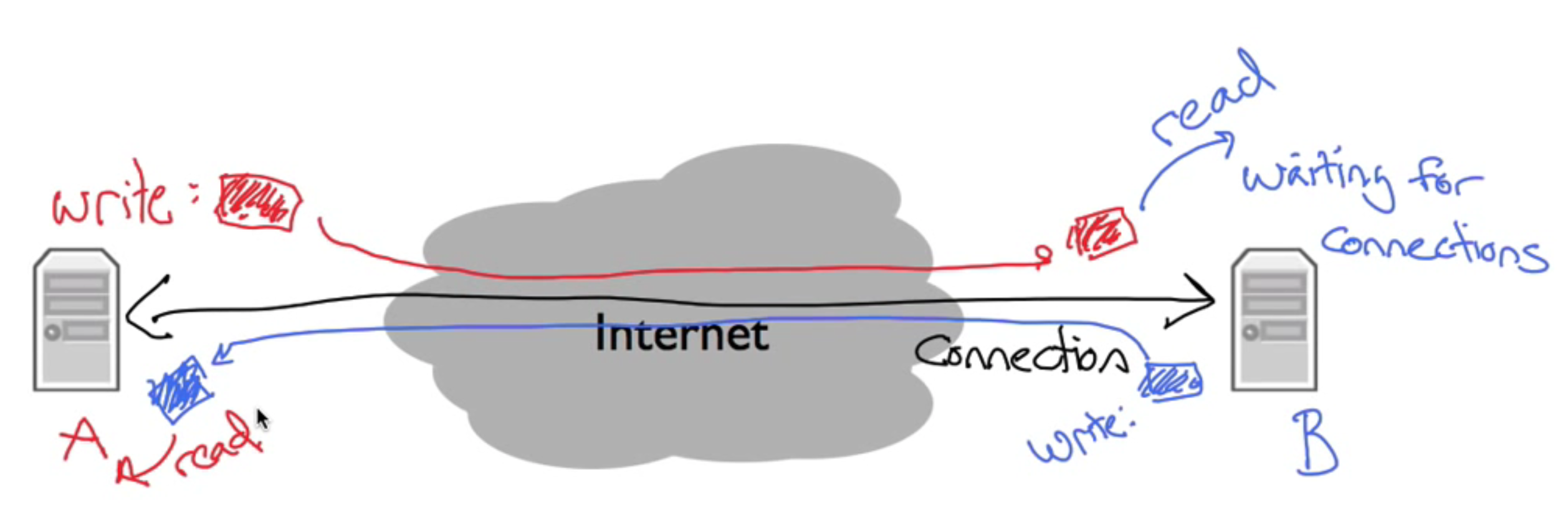
Dominant model now is : Bidirectional reliable byte stream connection
- One side read what the other writes
- Operate in both direction
- Reliable(Work on a connection)
For example the HTTP protocol works like this
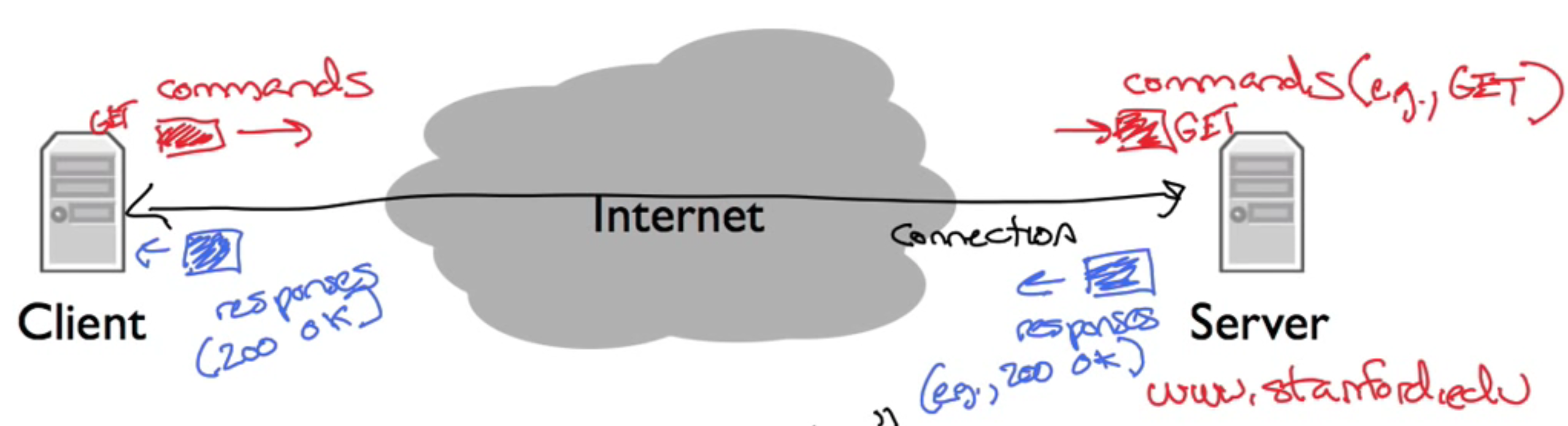
- Client open a connection to the server, the server accept the connection
- The client write the request to connection, the server read it from the connection
- The server write back the response to the connection, the client then read from the connection
The 4 layer Internet Model
Applications want to “use” the internet, they just care about read and write data, they don’t care how the data is transmitted. So they use layers as build blocks to reuse other people’s work rather than do all the thing from scratch
The model describe Internet operations in hierarchy
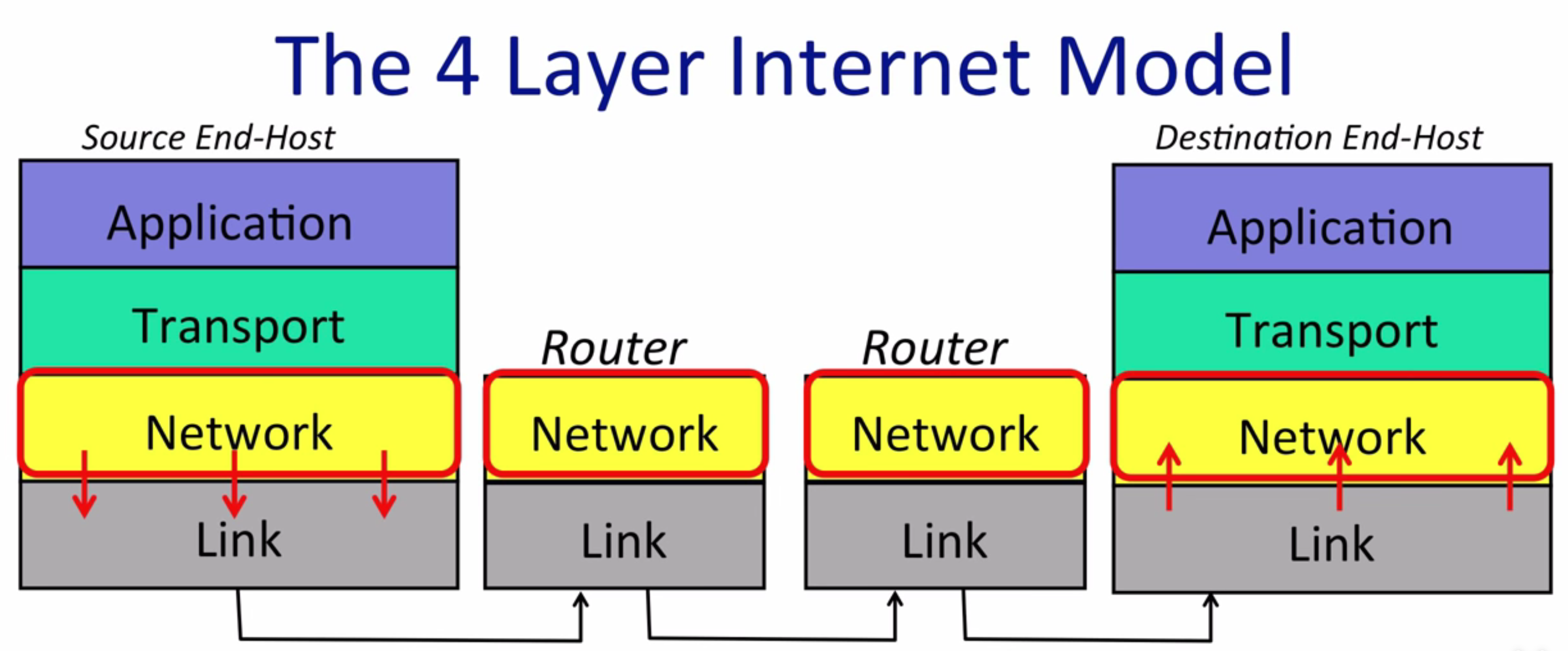
The link layer
The link layer is responsible for transmit the package
What is a package(aka datagram)?
2
3
| Data | from | to |
*----------------------------------------*
Link layer accept the package from network layer
Transmit one step forward, and then hand the package up to network layer
Network layer check whether itself is the destination of the package
1
2
3
4
5
6if (to_address == my_address){
accept();
}
else{
give_back_to_link_layer_and_transmit_to_next();
}The Network layer
The network layer is “special”, If you want to use the Internet, you must use IP(Internet Protocal)
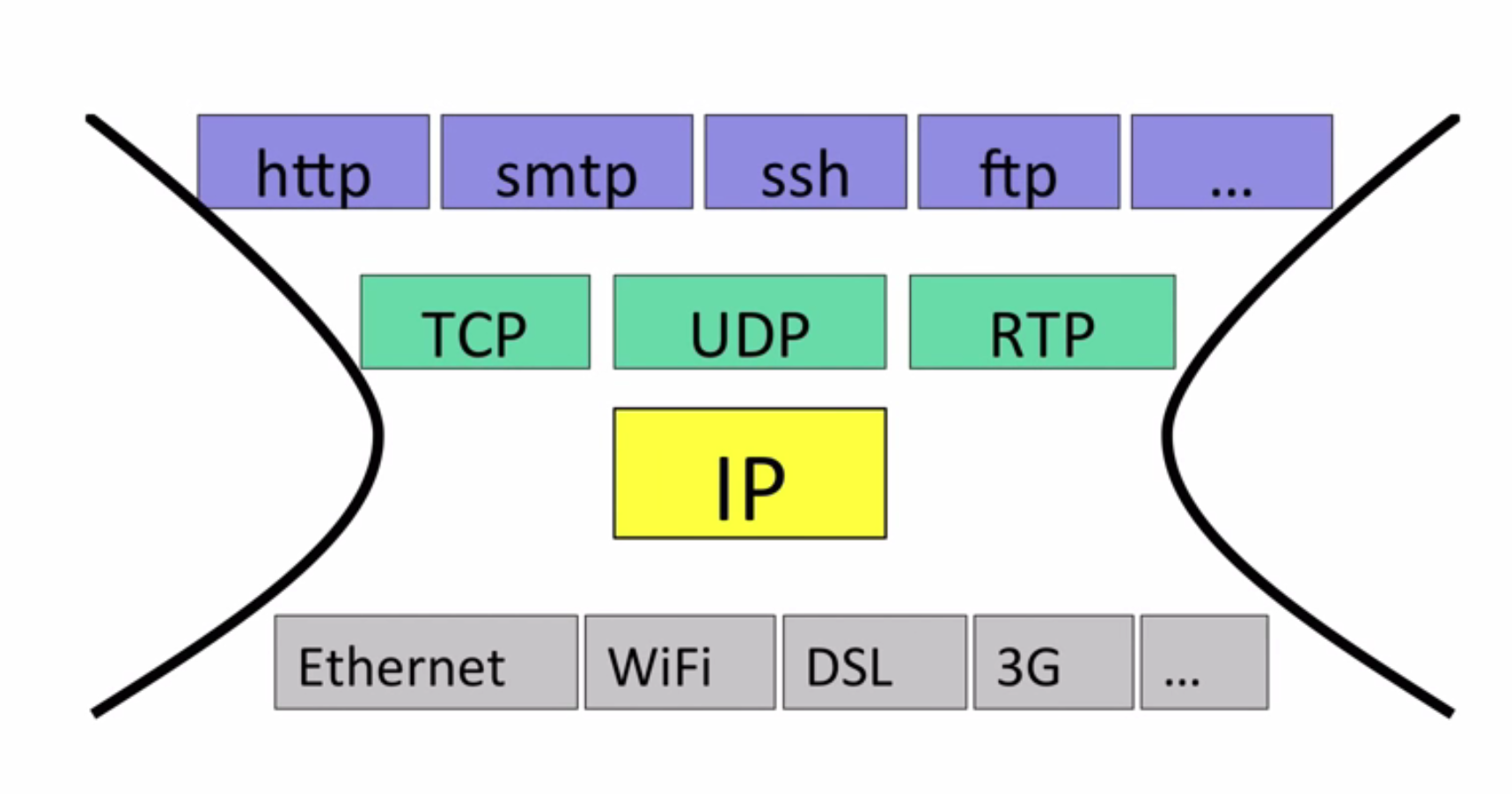
- IP makes a best-effort attempt to deliver the package to its destination, but NO guarantee.
- IP datagrams CAN be lost, CAN be delivered out-of-order and CAN be corrupted
If you want your data to transmit in a more controlled way, you should use another protocal running on top of IP —- TCP
The Transport layer
“Control” how the datagrams are transmitted
TCP(Transmit Control Protocol) do the “missing job” for IP
- If the datagrams are out-of-order, TCP will reorder them into the original way
- If there are missing and corrupted packages, TCP will ask the sender to resend they
However, not every application want a reliable transmit, they can use other protocals, for example UDP(User Datagram Protocol)
The Application layer
bidirectional byte stream
They can define their own protocols about how to interpret these bytes
Summary
4 layer model follows a horizontal way
Each layer pretend to talk “directly” to its peer layer, not knowing about what happens in the lower layers
4 layer model is an implementation of the OSI 7 layer model
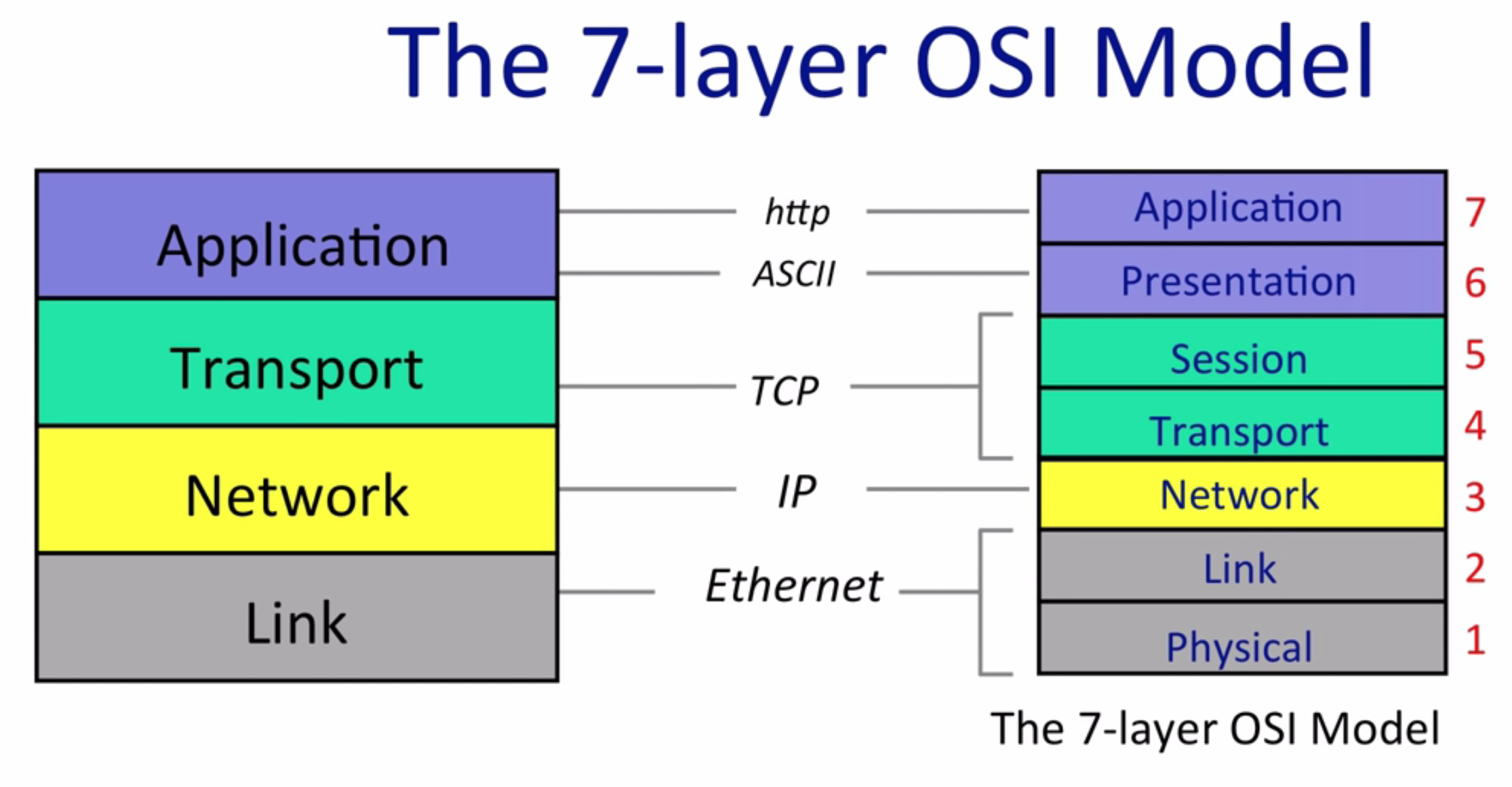
The only legacy to know about OSI model is the numbering system
Sometimes Application layer is refered as “layer 7”, link layer is refered as “layer 2” etc.